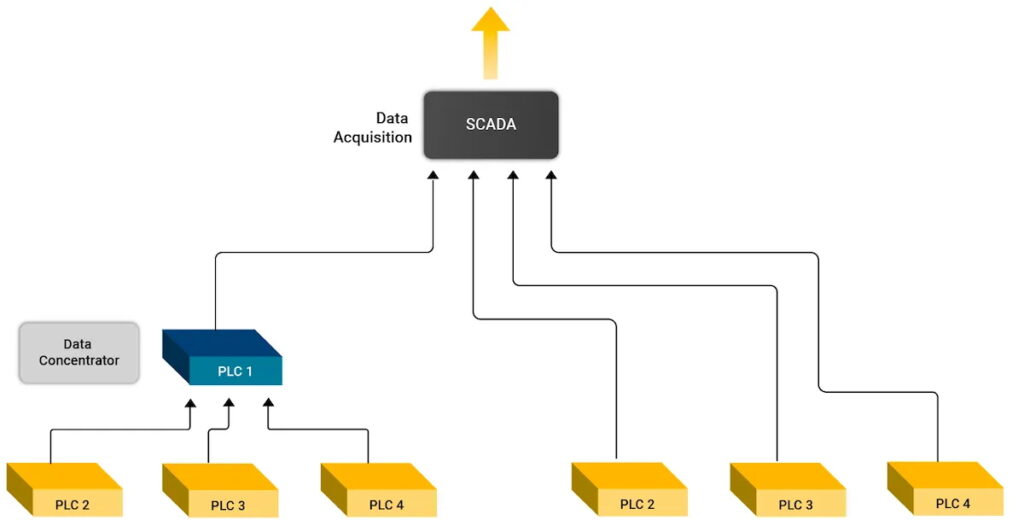
How SCADA Talks to PLCs — protocol translation, interfaces and practical engineering guidance
Modern industrial control stacks almost always pair on-site controllers (PLCs) with supervisory systems (SCADA). PLCs run the fast, deterministic control loops at the machine or process level; SCADA aggregates readings, provides operator HMI, alarms, historians and higher-level coordination. Getting these two layers to exchange data reliably and securely requires attention to three engineering domains at once: protocol semantics, physical interfaces, and operational security. Below I restate the essentials and then dive deeper into actionable patterns, common pitfalls, and practical selection rules for gateways/converters and network design.

Roles clarified: what PLCs and SCADA are responsible for
- PLC — real-time I/O scanning, local interlocks, machine sequencing. Millisecond-to-sub-second timing is typical; PLCs are the authoritative controllers for safety-critical loops.
- SCADA — supervisory monitoring, alarm management, trending/historian, operator control and supervisory setpoints. SCADA is not a substitute for PLC safety logic; it is the shop-floor’s “dashboard and dispatcher.”
Understanding this separation matters because it determines latency, reliability, and security requirements for the communication layer: control commands from SCADA must be validated by PLC logic; likewise, SCADA should not be relied upon for hard real-time control.
Communication building blocks: protocols, transports and semantics
Industrial ecosystems use many protocols and transports. Below is a compact mapping that emphasizes practical implications rather than marketing names.
| Protocol | Typical transport | Typical role (PLC / SCADA) | Engineering note |
|---|---|---|---|
| Modbus RTU | RS-485 / serial | PLC side common | Simple, ubiquitous; watch addressing, parity, and timing; polling model. |
| Modbus TCP | Ethernet / TCP-IP | Both | Easy to bridge; watch concurrency and transaction IDs. |
| PROFINET | Ethernet | Both (Siemens ecosystem) | High performance, vendor-specific features. |
| EtherNet/IP | Ethernet | Both | Industrial CIP object model; mapping and class/instance tags matter. |
| OPC UA | Ethernet / TCP (with TLS) | SCADA & middleware | Rich data modeling and secure channel options — preferred for modern integrations. |
| DNP3 / IEC 60870-5-104 | Ethernet / Serial | SCADA (utilities) | Wide use in power/water; supports event buffering. |
| CANopen / Profibus DP / CC-Link | Fieldbus / serial | PLC & field devices | Often used for local bus segments; requires converters to Ethernet. |
| BACnet/IP | Ethernet | SCADA (HVAC/building) | Building automation specifics. |
Two practical protocol points:
- Polling vs event/subscription: classic PLC-SCADA (Modbus RTU/TCP) is polling-centric. OPC UA and MQTT allow event-driven, subscription models that reduce polling load and lower latency for state changes.
- Data model mismatch: protocol converters must correctly translate not only bytes but semantic meaning (scales, signed vs unsigned, register packing, booleans vs coils).

Physical interfaces and connection modes
- Serial (RS-232/RS-485): cheap and robust, still dominant on legacy PLCs. RS-485 wiring topology, biasing and termination are common failure points.
- Industrial Ethernet: the backbone for modern systems — VLANs, QoS, L2/L3 segmentation apply.
- Wireless / Cellular / LoRa: used for remote assets; design for intermittent connectivity and secure tunneling.
- Hybrid: many sites have mixed serial + Ethernet devices; gateways that expose multiple physical ports greatly simplify cabling.
Options to bridge mismatches — when to use what
There are several distinct device classes engineers choose from; they overlap but each has specific strengths:
- Serial device servers (serial-to-Ethernet): give a serial port an IP address. Good when you just need remote access to an RS-485/RS-232 port. Limited protocol intelligence.
- Protocol converters: translate one industrial protocol to another (e.g., Profibus → Modbus TCP). They focus on mapping frames/registers and usually have little edge-logic capability.
- Industrial gateways / IIoT gateways: multi-protocol support, protocol translation, security features (VPN, TLS), edge compute (scriptable logic, data aggregation), store–and-forward and cloud telemetry. Best choice when integration requires security, buffering, or multi-tenant access.
- Data diodes / one-way devices: enforce one-way flow for high-security segments.
When to choose a gateway vs a converter: pick a gateway when you need data conditioning, buffering, user-management, and security features. Use a converter for straightforward, low-cost protocol translation without added logic.
Come-Star style gateway capabilities (recast as engineering features)
Multi-protocol engines support a wide range of industrial communication standards such as Modbus RTU/TCP, PROFINET, EtherNet/IP, OPC UA, MQTT, and DNP3, with built-in tag mapping tools that simplify cross-system data integration. On the hardware side, these devices are equipped with multiple physical interfaces, including RS-485, RS-232, and Ethernet ports, providing greater flexibility for on-site wiring. For remote deployments or environments with unstable networks, cellular-enabled models are available, featuring store-and-forward buffering to ensure data continuity during intermittent connectivity. In terms of security, they support TLS 1.2/1.3 encryption, VPN options such as OpenVPN and IPsec, as well as role-based access control, SSH, and certificate management, while avoiding legacy and insecure protocols like TELNET. Operationally, they offer advanced functions including heartbeat/watchdog mechanisms, serial and network caching, configurable polling rates, diagnostics and remote logging, local scripting for data transformation, and timestamping for historian correlation, ensuring stable and reliable performance in complex industrial environments.
Deeper engineering considerations (the things projects trip over)
- Timing & determinism: SCADA polling intervals vs PLC scan times — avoid using SCADA for tight control loops. For millisecond requirements, keep loop inside PLC.
- Throughput & polling load: naive SCADA polling of thousands of tags at short intervals can saturate gateways and PLC CPU. Use subscription/event models, increase caching, and group registers sensibly.
- Register mapping gotchas: pay attention to scaling factors, signed/unsigned conversions, register offsets (zero- vs one-based), byte/word endianness and combined 32-bit values. Test with simulators.
- Lossy links & buffering: implement store-and-forward and time-series buffering at the gateway so transient network outages do not lose critical events. Use sequence numbers or monotonic timestamps for data continuity.
- Command safety: write commands from SCADA should always be validated by PLC interlocks; implement command gating, deadman timers, and confirmation handshakes to prevent stale or repeated commands.
- Time sync: accurate timestamps are critical for historians and incident forensics. Use NTP/PTP and prefer PTP for sub-millisecond needs.
Security: practical prescriptions (not just buzzwords)
Industrial network security must be pragmatic and layered:
- Network segmentation: separate control, corporate, DMZ and remote access networks via VLANs and firewalls. Minimal allowed paths.
- Least privilege & RBAC: grant only the necessary operations per account or service. Audit and rotate credentials.
- Transport security: use TLS 1.2/1.3 for protocol channels (OPC UA, MQTT over TLS); disable weak cipher suites and TLS 1.0/1.1.
- Secure remote access: avoid exposing PLC ports to the internet. Use a hardened jump server, VPN with MFA and per-session auditing. Consider zero-trust solutions.
- Hardening & lifecycle: firmware signing, controlled patching windows, asset inventory (SBoM), and logging to SIEM for anomaly detection. Follow IEC 62443 guidance as an engineering baseline.
- One-way architectures where required: when data must flow out but never in, apply a hardware data diode.
Example deployment patterns (textual diagrams)
Simple legacy conversion
A Modbus RTU PLC (RS-485) → RS-485-to-Ethernet serial server (local) → Modbus TCP on LAN → SCADA.
Key notes: enable store-and-forward, set sensible Modbus polling groups, log serial errors, monitor bus termination.
Modern edge integration
Profibus DP device cluster → Edge gateway (Profibus master module) → OPC UA server (local) + MQTT telemetry to cloud (TLS) → SCADA/Historians subscribe to OPC UA or MQTT.
Key notes: expose an OPC UA information model for descriptive tags; use local rules to filter and aggregate high-frequency signals before cloud uplink.
High-security utility SCADA
Remote RTU (DNP3) → protocol gateway → DNP3 over TLS to SCADA master in DMZ → data diode into corporate network for reporting.
Key notes: prefer secure DNP3 variants and strong network segmentation.
Practical selection checklist for gateways/converters
When evaluating hardware/software, confirm:
- Supported protocols and simultaneous connections count.
- Physical port mix (how many RS-485/232/Ethernet).
- Throughput, max tags and polling intervals supported.
- Security features (TLS versions, VPN, RBAC, logging).
- Buffering and store-and-forward behavior during outages.
- Local logic/scripting capabilities for data conditioning.
- Management features (remote firmware update, diagnostics, SNMP/REST API).
- Ruggedness, MTBF, and certifications for your environment.
- Vendor support, life cycle and documentation quality.
Commissioning & operational best practices
A best practice for managing PLC–SCADA communication involves establishing a clear tag naming and mapping standard, where human-readable and consistent tag names are used. Canonical mappings should be maintained in structured formats such as CSV or JSON files to prevent ad-hoc lookups and reduce integration errors. Before deploying in a production environment, baseline tests are essential: simulating PLC responses and verifying gateway mappings ensures that configuration is correct and stable prior to connecting live systems.
Once operational, performance tuning should be performed by measuring latency and bus load under peak polling conditions. Parameters such as polling intervals, grouping of requests, and subscription modes should be optimized to achieve the right balance between responsiveness and network efficiency. Just as with PLC logic, change control is critical: all gateway or protocol modifications should be managed through version control, formal approval workflows, and defined rollback plans to mitigate risk.
Finally, robust monitoring must be in place. Gateways should expose health metrics including CPU usage, serial error counters, and connection status. These should be integrated into an alerting system so that degraded performance or failures can be detected early, ensuring continuous reliability and stability of industrial communications.
